Smart Integration Connector requires outbound traffic over port 443 to function. If you restrict outbound traffic over 443 then whitelisting outbound traffic to Azure Relay Service will be required. Smart Integration Connector does not require any inbound access rules to function.
 Learn how to whitelist traffic (2:33).
Learn how to whitelist traffic (2:33).
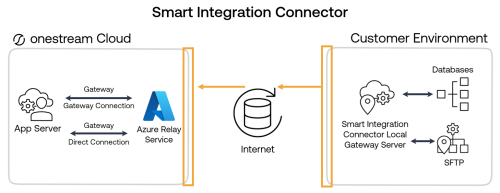
Restrict Traffic to the Azure Relay
You can block or restrict traffic to your Azure relay to only allow certain IP ranges to connect.
-
From the OneStream Windows Application client go to System > Administration > Smart Integration Connector > Relay.
-
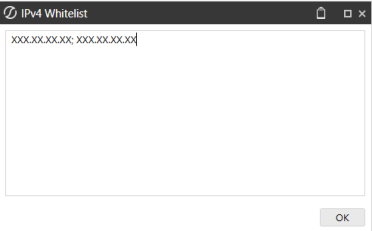
Select IPv4 Whitelist.
-
Enter IPv4 compatible IP (XXX.XXX.XXX.XXX) or CIDR addresses (XXX.XXX.XXX.XXX/XX) separated by a semi colon in the IPv4 Whitelist dialog box.
NOTE: IPv6 addresses are not currently supported.
NOTE: Do not include any extra spaces for characters.
-
Restart your Local Gateway Service.
Whitelist Outbound Traffic to Azure Relay Service from your Firewall
Allow outbound traffic using a wildcard domain to the Azure Relay Service (best practice). If the firewall does not allow wildcards, use the fully qualified domain names for your specific Azure Relay namespaces.
NOTE: For additional information, see Azure Relay WCF and Hybrid Connections DNS Support.
Allow Traffic using Wildcard Domain (Best Practice)
To allow traffic using a wildcard domain (Microsoft Recommended best practice), add *.servicebus.windows.net to the firewall rules permitting port 443 outbound.
Allow Traffic using IP addresses (Not Recommended)
To allow traffic using fully qualified domain names to the firewall rules:
-
Look up the IP addresses used by the Azure Relay namespace. The IP addresses can be returned by using this script.
-
Add the IP addresses to the firewall rules permitting port 443 outbound.
-
Frequently monitor the IP addresses for changes. Update the IP addresses in the firewall rules when there are IP address changes. The IP addresses can be returned by using this script.
NOTE: Up to 20% of the IP address can change in the span of a month. To ensure that Smart Integration Connector continues to operate, you will need to frequently monitor if these IPs change and adjust your firewall accordingly.


